With 1 in 2 organizations suffering a successful cyberattack over the past three years, the global cost of cybercrime in 2024 could reach $14.57 trillion (see References below for sources). 2023 represented a new high-water mark for cyberattacks like data breaches and ransomware, as detailed month by month in this PTP article.
On December 15th, the US government’s new SEC Rules also came into effect, requiring public companies to report on breaches within 4 days or face major consequences, and this is just one of the regulatory changes coming due to this stunning boom in cyberattacks.
With the threat landscape continuing to evolve, organizations must also continually adapt to keep up. But as Kirk Hasty, a Senior Technical Product Manager at Carbon Black suggests, the human element remains central to any initiative:
“We have talked to our customers about supply chain attacks, keeping vulnerabilities identified, patched, and remediated as soon as possible, and consistently focusing on this. It is important to keep end users trained on things like being diligent when checking emails or clicking on links and not making rash decisions when an email or phone call pressures them to make a quick decision.”
In today’s PTP Report, we look into three cybersecurity trends for the 2024 year: the reality of emerging Zero Trust Security, AI-powered threats and defenses, and the ever-increasing demand for (and lack of) cybersecurity experts.
Zero Trust Security Is Now for Real
Many traditional cybersecurity systems have been strained, or even broken, by the increase in remote workers and the geographic distribution of teams, as detailed in this PTP piece.
As Hasty says:
“In the past, many companies depended on perimeter-based models like a firewall. While a firewall is still useful, it is less effective in today’s environment because users access systems from various locations and devices, which are often outside the organizational perimeter.”
So-called Zero Trust models are not new—the idea of not trusting, but always verifying system users dates back more than 25 years—but to date, they’ve often been more theoretical than practical. The goal is for no entity inside or outside a network to be trusted by default.
Kirk Hasty:
“Traditional security models are often more like a piecemeal strategy. While having different tools and protections can be helpful, it can also create security gaps. Companies often customize their strategies using various components and software that might not integrate seamlessly, leading to problems and additional vulnerabilities on their network.”
With a Zero Trust approach, users must explicitly verify who they are, and that they have a right to be where they are, not where they are.
When an inevitable breach occurs, there is a continued requirement for verification, and restricting individual user access to only what they need for a given role, greatly limits the spread of damage, like the kind discussed in this PTP piece.
Building a Zero Trust system requires buy-in from across departments, and can be difficult to implement, but it’s increasingly viewed as a key means of dealing with a widely distributed workforce, teams, and systems across organizations.
With no clear borders to protect, one can no longer assume anyone moving through an organization’s system has the right to be there.
The Russian proverb “trust, but verify” may be too generous as we look to the future. Distrust, and keep verifying may be more apt.
AI-Powered Threats and Defenses
 Kirk Hasty:
Kirk Hasty:
“There is a growing use of AI tools by cyber attackers to craft more convincing and sophisticated attacks. They can leverage the data of successful and unsuccessful attacks and breaches, adjust quicker, and leverage tactics that have worked in the past.
There are attackers now using AI to generate next-level phishing attacks. Phishing is one of the most effective methods, but attackers continuously refine their phishing techniques, making them more difficult to detect.”
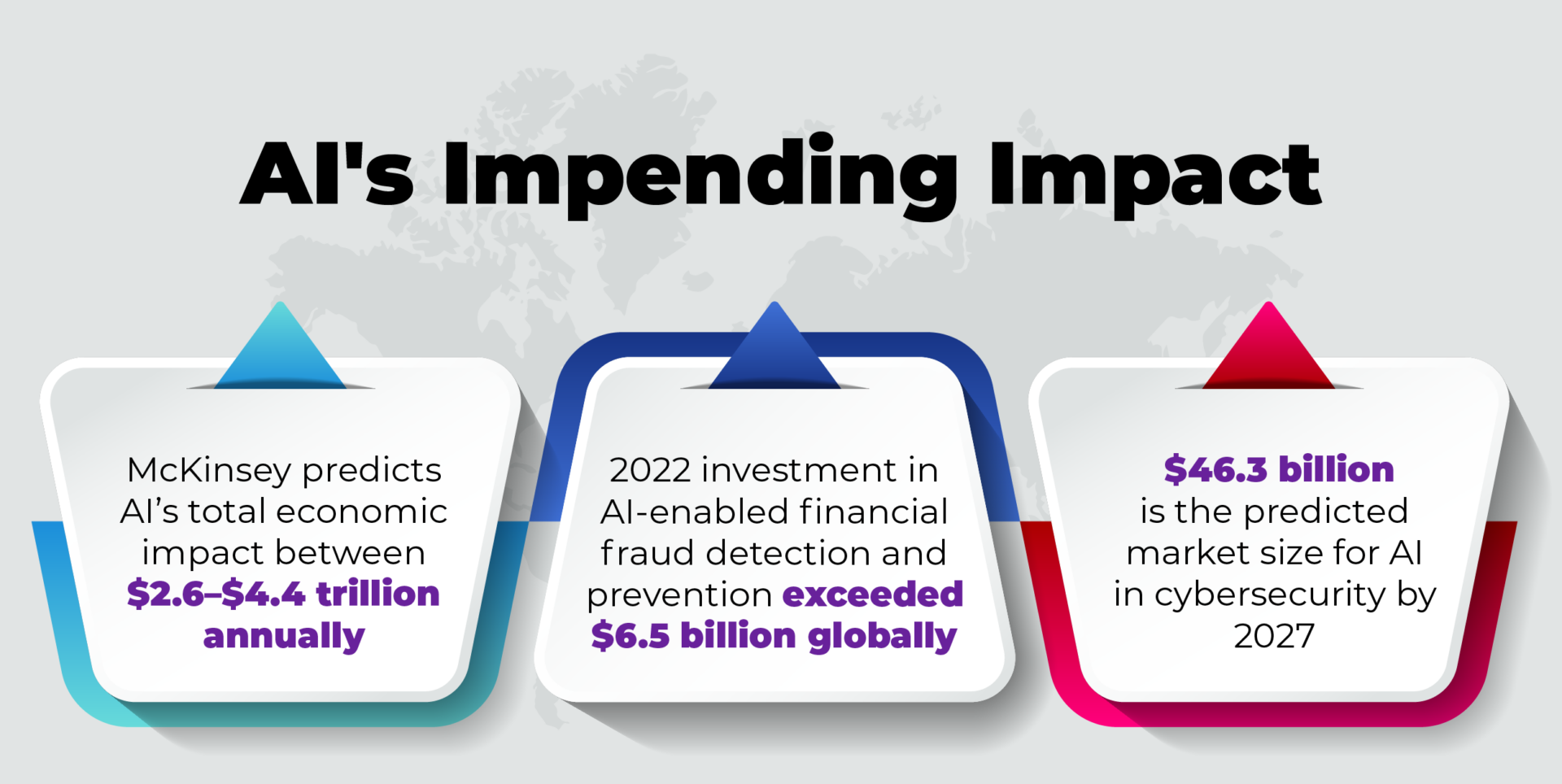
As the breakthrough innovation and cultural phenom of 2023, AI is no longer new, even as its impact on security continues to evolve.
Tools like WormGPT and FraudGPT help even casual hackers leverage AI’s power for cybercrime, while conventional chatbots like ChatGPT can help phishers create more convincing emails. AI art tools make it easy to build more convincing graphics, logos and deepfakes, to snare unwary targets.
AI can also be used to accelerate the search, recognition, and means to exploit an organization’s vulnerabilities. And it can even craft customized malware to take advantage. [Check out this PTP article for a look at some of these AI-specific security risks]
But just as organizations need to stay vigilant against AI risks, they also must harness its power to fight back.
“Organizations [must] also leverage AI for enhanced cybersecurity defenses to help detect patterns and tactics,” Carbon Black’s Kirk Hasty says.
“This calls for enhanced vigilance, advanced detection methods, and training for cyber defenders to use AI technology to enhance and improve their cybersecurity defenses.”
It also requires working across teams, to stay abreast of how AI is being used. I can be used to analyze one’s own vulnerabilities, and even simulate attacks.
Just as AI helps hackers find weaknesses, it can also help organizations find and patch them, stay alert to attacks and outages, and rapidly accelerate their responses.
[See this PTP piece for how AIOps can be used to boost the power of SRE in helping to fight back]
Cybersecurity Workers in Demand
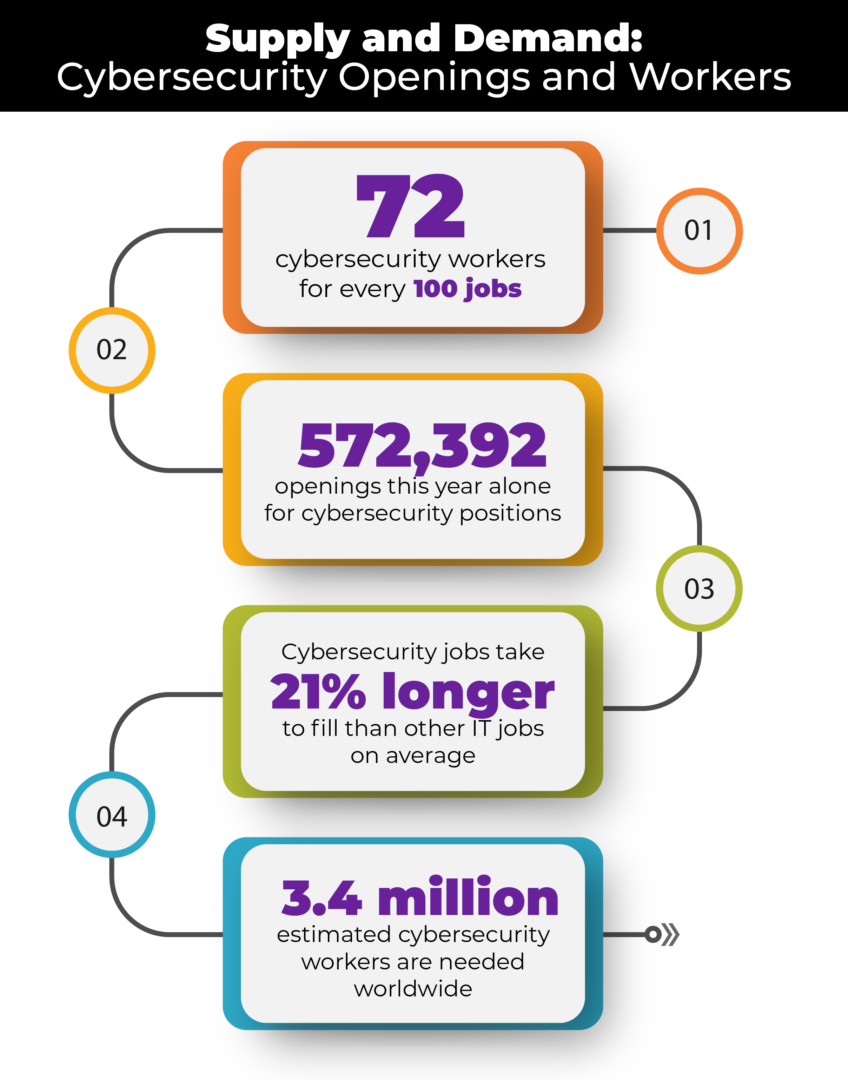
Given the rise in attacks, it’s probably not surprising that trained cybersecurity workers are in high demand, nor that 64% of leaders surveyed by the World Economic Forum see recruitment and retention of cybersecurity personnel as a critical challenge in fixing this problem.
Hasty: “The demand for skilled cybersecurity professionals is increasing, highlighting the need for more specialized training and certifications.”
Sites like US government-collaboration cyberseek.org are wholly dedicated to this end, working to aid students on the career pathway and to pair workers with organizations in need. With a 30% year-over-year growth (2.4 times faster than all jobs), it’s not a problem expected to ease any time soon.
Keep an eye on the PTP Report for an upcoming article about this need, with advice for getting started in cybersecurity in 2024, and if you’ve already got these skills or are on the look at your organization, consider PTP to speed you on your way!
Conclusion
Carbon Black’s Kirk Hasty expects that in 2024, a “greater emphasis and dependence on machine learning, cloud security, and AI, will continue.”
Also expect Zero Trust models, long considered an intriguing means to protect distributed teams, to continue to be implemented, and improved on. As Microsoft says of its own Zero Trust initiative: “verify explicitly, use least-privilege access, and assume breach.”
AI is here to stay. But there’s no reason attackers alone should have the full use of its advantages. AI solutions give leaders who stay abreast of its development and keep in touch with their in-house use of their own potent tool. It can help them predict attacks, better monitor and protect their systems, and respond far more rapidly when they inevitably occur.
And finally, passionate cybersecurity professionals are an increasingly essential resource that must be nurtured, maintained, and empowered in this escalating war against cybercrime.





 Work with us
Work with us